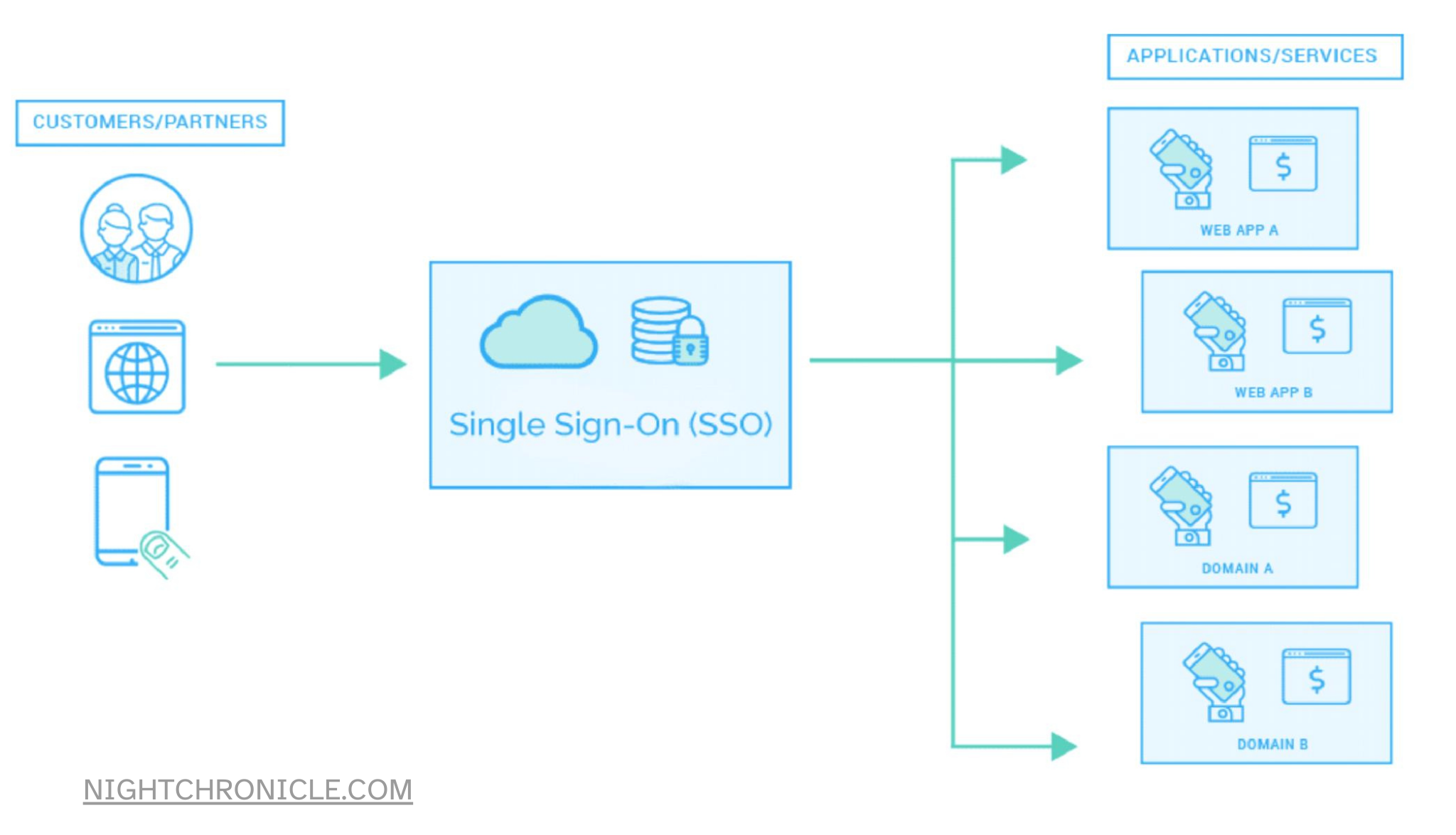
Introduction
In the current digital era, controlling user access to diverse online resources is essential to the effectiveness and security of an organization. Businesses, academic institutions, and governmental organizations looking to streamline user authentication procedures while enhancing security now consider Single Sign-On (SSO) solutions to be indispensable resources. This piece will examine the notion of CISD SSO (Centralized Identity and Single Sign-On) and examine the ways in which it is transforming authentication and access control across multiple industries.
Understanding SSO and Its Importance
In the digital realm, user authentication is required to use many services, including email, file storage, productivity tools, and software applications. It was challenging and time-consuming for users to log in to each of these services separately in the past, often requiring different usernames and passwords.SSO addresses this issue by allowing users to access multiple services with a single set of credentials. SSO improves user experience, lessens password fatigue, and lowers the possibility of security breaches brought on by weak or repurposed passwords by streamlining the login process.
The Role of Centralized Identity
Centralized Identity is the foundational concept behind CISD SSO. It involves managing user identities from a central repository, ensuring consistency, and simplifying identity and access management. This approach is particularly valuable for large organizations with numerous users and diverse resources.
The key components of Centralized Identity in CISD SSO include:
2.1. User Directory
- Putting away client data, for example, usernames, email locations, and gathering affiliations in a focal registry.
- This registry can be facilitated on-premises or in the cloud, contingent upon the association’s requirements and inclinations.
-
2.2. Identity Verification
- Checking the character of clients through different techniques, for example, username and secret key, multifaceted verification (MFA), biometrics, or savvy cards.
- Multifaceted validation upgrades security by expecting clients to give more than one type of check.
Advantages of CISD SSO
Organizations aiming to enhance access management and security find cisd sso to be a compelling option due to its numerous advantages. Among these benefits are the following:
3.1. Enhanced User Experience
- By eliminating the need for users to remember multiple sets of credentials, SSO simplifies the login process, reducing user frustration and increasing productivity.
3.2. Increased Security
- Centralized Identity provides a robust security foundation by enabling organizations to implement stronger authentication methods like MFA.
- It also simplifies the revocation of access, making it easier to respond to security threats.
3.3. Cost Savings
- With reduced helpdesk calls for password resets and improved user productivity, organizations can realize cost savings.
3.4. Compliance
- CISD SSO can help organizations meet compliance requirements by providing robust identity and access management controls.
- Implementing cisd sso
Deploying CISD SSO involves several steps, including:
4.1. Assessing the Environment
- Understand your organization’s existing systems, resources, and user access requirements.
- Determine which applications and services will be integrated into the SSO solution.
4.2. Choosing a CISD SSO Provider
- Evaluate SSO providers based on factors such as scalability, security features, cost, and compatibility with your existing systems.
- Popular CISD SSO providers include Okta, OneLogin, and Microsoft Azure Active Directory.
4.3. Designing the SSO Architecture
- Create a plan for integrating the selected cisd sso solution into your environment.
- Consider factors like user roles, application integration, and security policies.
4.4. Testing and Deployment
- Thoroughly test the SSO solution in a controlled environment before rolling it out to all users.
- Develop a deployment strategy that minimizes disruptions to your organization’s daily operations.
4.5. User Training and Support
- Give preparing to clients on the most proficient method to utilize the new SSO framework.
- Guarantee that your IT support group is ready to help clients with any issues that might emerge.
CISD SSO has applications in various sectors, including:
5.1. Education
- Educational institutions can use SSO to simplify access to learning management systems, student portals, and other resources.
- Enhanced security measures protect sensitive student data and intellectual property.
5.2. Healthcare
- In the healthcare sector helps medical professionals access patient records and healthcare applications securely.
- HIPAA compliance is easier to maintain with centralized identity and access controls.
5.3. Government
- Government agencies can improve the efficiency of their operations by implementing cisd sso for government employees.
- For the sake of national security, secure access to government systems and classified information is essential.
5.4. Business
- Organizations across all industries benefit from CISD SsO, as it streamlines access to productivity tools, cloud services, and business applications.
- It enables secure remote work, a crucial feature in the modern workplace.
- Challenges and Considerations
While CISD SSO offers numerous advantages
6.1. Integration Complexity
- Integrating various applications and systems into the SSO solution can be complex and time-consuming.
- Compatibility issues may arise.
6.2. Data Security
- Centralized identity repositories become high-value targets for cyberattacks.
- Robust security measures are essential to protect sensitive user data.
6.3. User Adoption
- Not all users may immediately embrace the new SSO system, requiring organizations to invest in user training and support.
- Future Trends in SSO
Some future trends in CISD SSO include:
7.1. Zero Trust Security
- Zero Trust security models will become more integral to cisd sso solutions, emphasizing continuous authentication and access controls.
7.2. Improved User Experience
- Development will be centered on the user experience, with a goal of achieving the most seamless and user-friendly authentication possible.
7.3. AI and Behavioral Analytics
- AI and behavioral analytics will play a significant role in enhancing security, with the ability to detect anomalous user behavior and respond proactively.
-
Conclusion
CISD SSO represents a significant step forward in the realm of identity and access management. By centralizing user identities and streamlining the authentication process, organizations can improve both efficiency and security.Even though there are obstacles to overcome, CISD SSO implementation has significant advantages, making it a crucial option for any organization looking to improve its digital operations.
Organizations need to keep up with the newest security procedures and technologies as the digital landscape changes. In order to handle the recurring difficulties with user access management, cisd sso provides a dependable and all-inclusive solution that eventually opens the door to a more effective and safe future.
FAQs
What are the key components of Centralized Identity in CISD SSO?
The key components of Centralized Identity in CISD SSO include a user directory, identity verification methods (e.g., multi-factor authentication), and centralized management of user attributes.
READ ALSO:
Trendzguruji.me Health: The Future of Healthcare is Here